Process Monitor
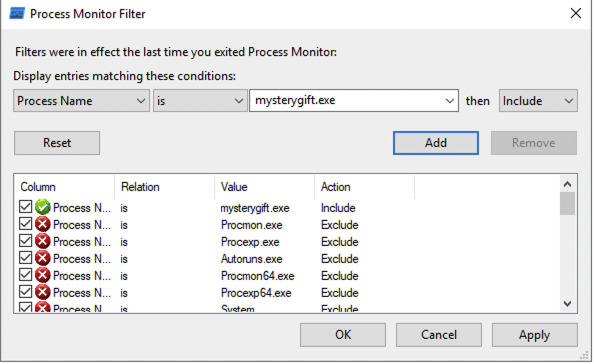
Process Monitor Filter is a feature that allows us to filter the results logged by ProcMon. In this case, we want to only focus on events generated by mysterygift.exe process. Let's set the condition Process Name - is - mysterygift.exe ; add the filter and choose OK to close the prompt.
Now, let's prepare the malware sample for execution and rename it to mysterygift.exe.
C:\Users\Administrator\Desktop\Malware Sample>mv mysterygift mysterygift.exeWe are now ready to pop the malware. Navigate to the Malware Sample folder, double-click the binary and observe the results generated by ProcMon. It might be overwhelming at first but let's utilise its functionalities to only show the information we want.
ProcMon has a panel that can filter the following, as highlighted in the image below (in sequence):
- Show Registry Activity
- Show File System Activity
- Show Network Activity
- Show Process and Thread Activity
- Show Profiling Events
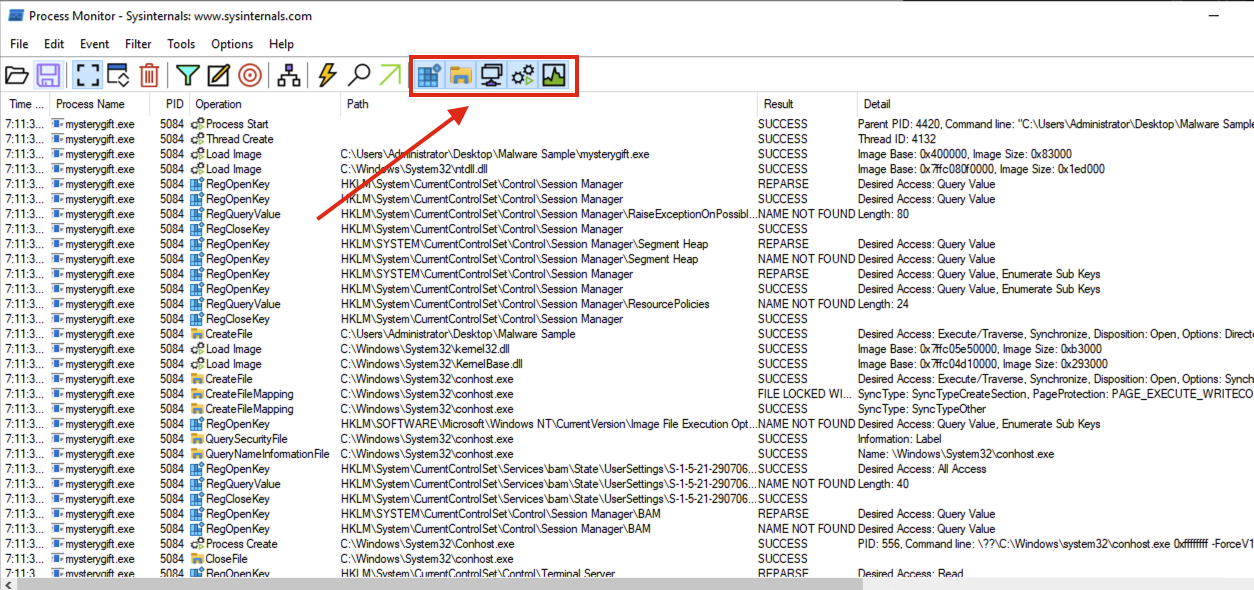
With these filters, we will focus on the first three; Registry, File System and Network.
Registry Modification
First, we want to determine if any significant Registry Modifications are executed by the binary, which is one of the expected behaviours introduced in this task.
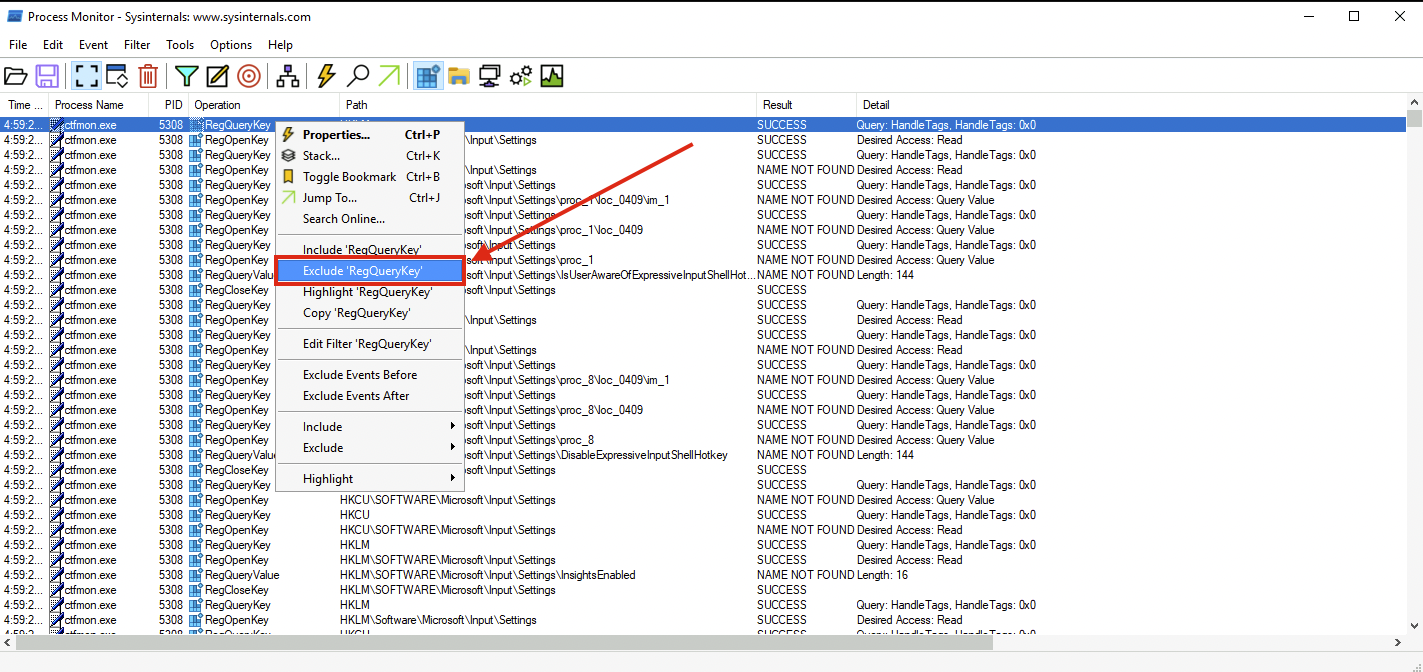
To do this, unclick all filters and only choose Show Registry Activity. The results still give several results so let's add a filter by finding all Registry Key Creations and Modifications. Remove the following Operations by right-clicking an entry from the Operation column and choosing Exclude '<operation (e.g. RegQueryKey)>' similar to the image below:
- RegOpenKey
- RegQueryValue
- RegQueryKey
- RegCloseKey
The view from ProcMon should yield fewer results, similar to the image below.
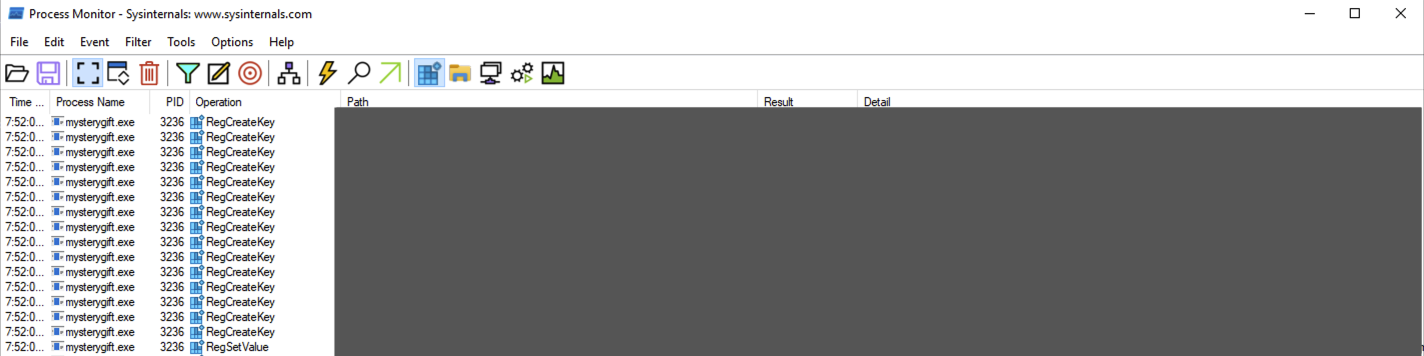
You may observe that only one Registry Key has both RegCreateKey and RegSetValue. This key is related to a persistence technique called Registry Run Key Modification and is commonly used by malware developers to install a backdoor.
File Modification
Now, let's also determine if the malware sample executes File Creations. It may indicate that the malware drops prerequisite files for its successful execution.
Unclick all filters and choose the second filter - Show File System Activity. Again, the results are still numerous so let's add extra filters by focusing only on File Write events. Remove the following Operations again by right-clicking an entry from the Operation column and choosing Exclude '<operation (e.g. CreateFile)>':
- CreateFile
- CreateFileMapping
- QuerySecurityFile
- QueryNameInformationFile
- QueryBasicInformationFile
- CloseFile
- ReadFile
The view from ProcMon should yield fewer results, similar to the image below.
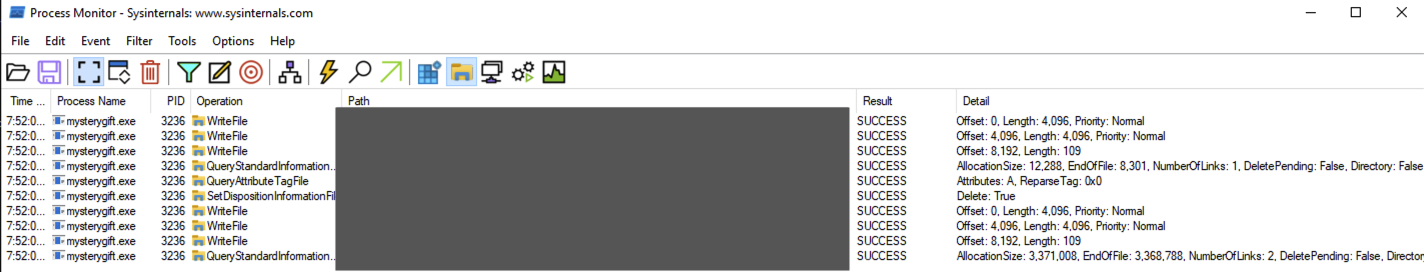
You may observe that two files are written under the C:\Users\Administrator directory. The first file is located in the user's TEMP directory, which is commonly used by malware to drop another file for its disposal. The other file is written in the STARTUP directory, also used for persistence via Startup Folders.
Network Connections
Lastly, let's confirm if the malware sample attempts to make a network connection. It may indicate that the malware communicates with external resources to download or establish remote access.
Unclick all filters and choose the third filter - Show Network Activity. Unlike the previous filters, the results are few and can be easily interpreted.
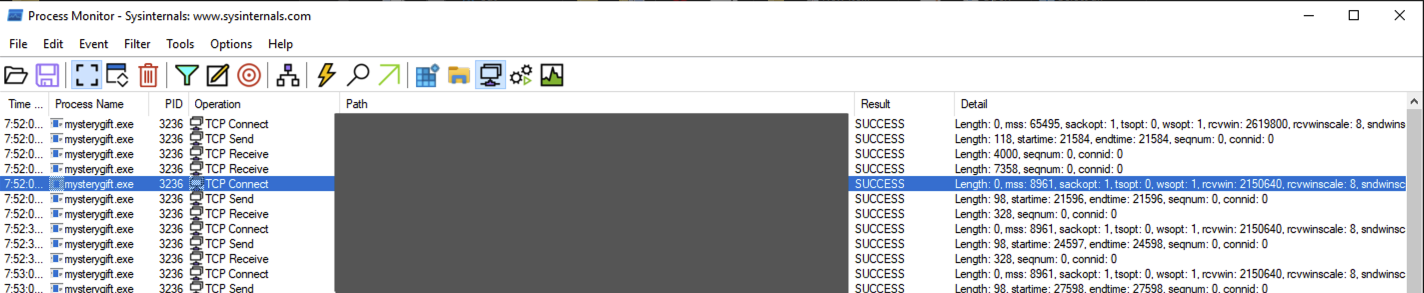
Please take note of these domains, as we can use this information to investigate the rabbit hole further.